Open-Source Internship opportunity by OpenGenus for programmers. Apply now.
Reading time: 10 minutes
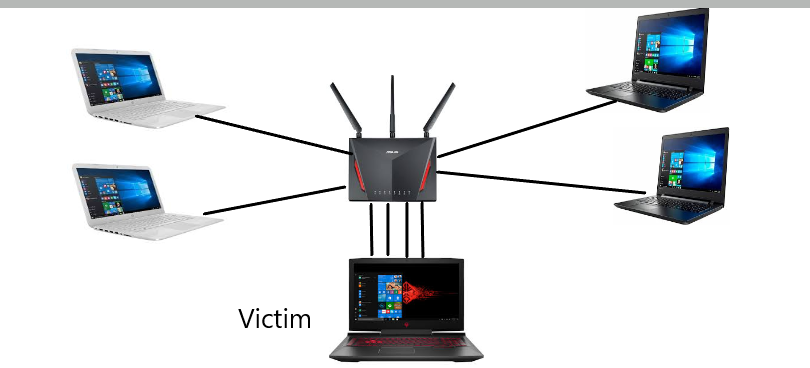
Ping of Death (PoD) Attack is a form of DDoS attack, which is used for disrupting the victim network by sending the packets larger then the max size allowed using some arbitrary commands. The attack degrades the targeted system or even freeze the system.
Procedure For The Attack
- For this attack to happen the hacker first transmits the large sized packets to the victim system.
- The packets then become fragmented each of which is of max size limit. When the victim system puts the pieces of the packets together.
- The total of the packet size exceeds the size limit and a buffer overflow occurs. Finally, the attack crashes the system or degrade the performance of the system.
Image For Understanding The Attack
Mitigation For The Attack
The avoid this type of attack:
- block the fragmented pings
- filter the actual pings traffic
- block all the listening ports where the invalid packet attacks can come from
- block the ICMP ping messages at the firewall
MCQ Round
Question 1
What is PoD
Ping Of Dawn
Ping of Dust
Ping of Death
Packet of Death
Question 2
Which Vulnerability can occur from this attack?
RCE Vulnerability
Buffer Overflow
CSRF Vulnerability
XSS Vulnerability