Cryptography in Bitcoin
In this article, we learn about the different types of cryptography. We also learn why public-key cryptography was chosen for Bitcoin.
Table of Contents.
- Introduction.
- Symmetric Cryptography.
- Asymmetric Cryptography.
- Cryptographic Hashing.
- How Bitcoin uses Public-key Cryptography.
- Summary.
Introduction
In blockchains specifically Etherium and Bitcoin, two techniques are used in the validation and verification of transactions and the security of the chain. The first is hashing and the second is asymmetric key encryption.
Remember, on public blockchains, all transactions are public but users can decide to stay anonymous. This poses a huge security risk since in order for it to work trust has to exist between participants. These and most issues involved with the blockchain are solved with cryptography.
First, it is important to note that cryptography is the foundation upon which a secure decentralized blockchain operates. As discussed in a previous article Ethereum has two types of accounts, EOAs and contract accounts. To be able to participate in the network, one is required to have an EOA which is acquired through digital private keys which are at the heart of all transactions on the network.
Access and control to funds are possible through digital signatures which are also generated using private keys. This means anyone with the private key has control over the corresponding account.
There exist three major types of cryptography, symmetric, asymmetric, and cryptographic hashing.
Symmetric Cryptography.
Symmetric cryptography was the first to be developed, the idea is simple, we hash a text using a key into a cipher, and to decrypt it, we use the same key.
In other words, we use the same key to encrypt and decrypt a message. This means that the people communicating with each other had to find a way to exchange the key securely so that it could be used for the decryption process.
For this type of encryption, data was scrambled and made impossible to read by anyone who did not possess the key. Once the key was delivered to the recipient, the algorithm used it to reverse the encryption process to obtain the plain text message.
The secret key used for this process could be a password or secret code that both knew or they could use a random number generator to generate a random key to encrypt the message.
There exist two types of symmetric encryption, these include;
- Block algorithms - this is whereby a set of bits is encrypted in blocks of electronic data using a secret key.
- Stream algorithms - This is whereby data is encrypted in streams of data instead of blocks.
Examples of asymmetric forms of encryption include; Advanced Encryption Standard(AES), Data Encryption Standard(DES), Blowfish, Rivest Cipher 4, 5, and 6 among others.
This although effective for small-scale tasks and applications is not as safe for large-scale applications where a lot of sensistive data is being transferred. For example, while transferring the key, it might be sniffed by malicious users. Also executing a brute force attack on such encryption is very easy with the computational power available nowadays.
Asymmetric Cryptography.
Also referred to as public-key cryptography is commonly used in modern technology in many ways for encrypting data e,g in network packets, communication protocols, and services such as ssh, sftp, RSA, etc. All these use asymmetric cryptography whereby we generate two keys, a public, and a private key. The public key is shared and known by all parties while the private key remains private. This however doesn't assure 100% security, the private key can still be acquired through other means such as social engineering or hacking.
The following image summarizes the concept of public-key cryptography;
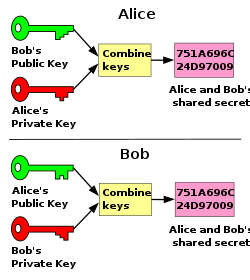
Consider the following scenario, participants A and B both have generated public and private keys. For them to share an encrypted message, A sends to B, A encrypts the message using her private key and B's public key. Note that the public keys are public knowledge but in order for B or any other user to decrypt the message, he needs his private key together with A's public key. This means that if B lost his private key, and since the public key is public, the malicious user has control over the bitcoin wallet.
Unlike symmetric forms of cryptography such as caesar's whereby once a text was Encrypted it could be reversed, asymmetric cryptography makes it easy to encrypt but once encrypted, the encryption is irreversible, a new key apart from the one used to create the encryption is needed. That is, the multiplication of two big prime numbers is somewhat trivial while a factorization of the product is a computationally demanding task that could take years, long enough past our existence.
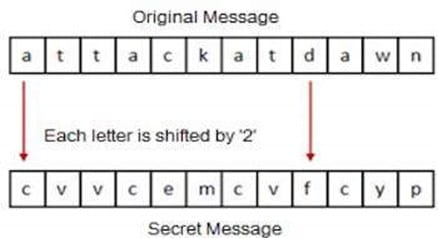
Here alphabets are shifted by n referred to as the key. The same key is needed to decrypt. This could be cracked in two ways, first, we can get the key from the encrypted text using brute force, second sharing the key is risky, and hackers can sniff the key.
Cryptographic Hashing.
The final type of cryptography is referred to as cryptographic hashing, this is whereby a text goes through a hashing function/algorithm e.g, SHA to come up with its equivalent hash. Now it is harder to know what the original text was. This is commonly used for storing user passwords on databases. A major benefit of hashing is that we can reduce any number or length of text into s fixed-size hash, e.g, a 128-bit hash.
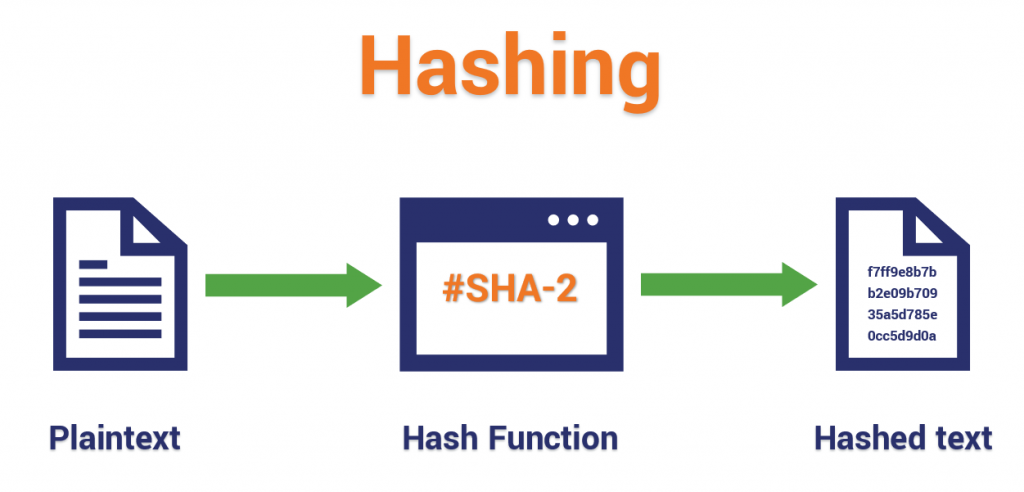
A cryptographic hash function is a mathematical algorithm that takes an arbitrary length of data and maps it to a fixed-size bit array referred to as the hash value.
This function is one-way meaning that it is easy to go one way(encrypt) and impossible to reverse(decrypt) using the same parameters.
The only way that one could crack this encryption is to find a similar message that produces the same hash by using a brute force algorithm that cycles through all possible inputs. Here we can also use a rainbow table of previously matched hashes.
Cryptographic hash functions are deterministic in nature meaning that the same message always produces the same hash value.
Some of the properties of a such a function include;
- Easy to compute - takes less computational resources.
- Resistant to collisions - two different messages should not produce the same hash
- Output cannot be used to reveal the input.
- Irreversible.
How Bitcoin uses Public-key Cryptography.
As mentioned blockchains such as bitcoin use ECC cryptography since it is harder to crack. Once a pair of public-private keys are generated. The public key combined with a hash function is used to generate a wallet's address. This is the interface for users to the blockchain network.
On the other hand, the private key is used to sign digital transactions, these keys should not be disclosed to the public. Digital signatures just like hard signatures on hardcopy documents are used to verify the signer is the account holder holding the private key. These signatures are at the core of every transaction made on the bitcoin blockchain.
Elliptic-Curve Cryptography
Ethereum as well as bitcoin blockchains use the ECC cryptographic protocol which is just another implementation of public-key asymmetric cryptography just like RSA but a better and more secure. ECC allows for smaller but more powerful keys which provide even better security compared to larger RSA keys. That is;
256 bits of ECC key pair is equivalent in strength to 3072 RSA key pair bits.
Its security is based on the ability to compute a point multiplication and the inability to compute the multiplicand given the original and product points.
The public-private key pair in Ethereum represents an account, it provides the account's public address and private control over the account to ether in the account and needs involving smart contracts.
Summary
Public keys can be derived from private keys. ECC - Elliptic Curve cryptography is used on bitcoin and Ethereum blockchains.
Symmetric encryption is faced with key distribution and the same key issues. These are resolved by asymmetric cryptography where two keys will exist between both parties.
A 256-bit ECC public-private key pair is equal in strength to 3072-bit RSA key pair. This not only means ECC produces shorter keys for any length of the message but ECC is also very hard to crack.