Mining and Spending Transactions
After a transaction is created and propagated across network nodes. It has to be validated, verified and added to a block - (mining). In this article, we learn how this is done and how transactions can be spent.
Table of contents.
- Introduction.
- Mining transactions.
- Spending a transaction.
- Double spending.
- Summary.
- References.
Prerequisites.
Introduction
In the previous article, we saw how transaction inputs and outputs are generated on bitcoin and also how they are propagated. However, this is not the end, the transactions have to be validated, verified then added to a block, a process referred to as mining.
Mining results in new coins being brought into circulation. For a transaction to be mined, a significant amount of computational power is needed, in return to miners for providing the resources to sustain the network, Bitcoin offers incentives when a new block is created.
The process of mining on the Bitcoin blockchain results in the creation of new coins. The amount of bitcoin that can be mined is limited. At some point, it will be all mined and in circulation. Having a limited number of bitcoins ensures it is resistant to inflation. To this extent we can compare mining to printing money in traditional financial institutions only in this case, any amount can be printed and put in circulation.
All transactions on Bitcoin are charger transaction fees, this is a fee given to a miner as payment for processing and validation of a transaction. Miners earn in two ways, first by getting rewarded with new bitcoins and second by the transaction fees.
Once a puzzle is solved the next competition to solve the next begins. The winner earns the right to create the next block and all previous miners reach a consensus to add the newly created block into the chain.
The increase of miners in a network means more network security as transactions have to be validated by all. This means a higher hash rate and therefore the computing needed to solve the puzzle can no longer be provided by even GPUs, miner opt for ASIC chips which are computer chips specifically programmed with mining algorithms
Miners also have to perform an economic evaluation to decide if it is profitable to mine bitcoin. This is because just like any currency bitcoin is affected by supply and demand. When the demand is high, the network is booming and has a large number of miners and the hash rate is higher and which means more security, immutability, and decentralization. However, when the markets are down, a miner can choose to use their hardware to mine a more profitable coin. Such situations can introduce vulnerabilities whereby a single party manages to acquire 51% of network nodes. In future articles, we will discuss how this is managed in robust blockchains such as Bitcoin and Ethereum.
Mining transactions
As mentioned earlier, transactions are stored in blocks. At any minute there could be millions of transactions being processed on the network, before they can be incorporated into the blockchain, they are first stored in a pool of unverified transactions. Miners mine the transactions into a block then other miners reach a consensus about adding the new block with new transactions to the chain. The consensus algorithm is referred to as the Proof of Work(PoW) algorithm, this and many others such as;
- Proof of Stake(PoS) - Used by Ethereum 2.0. This is whereby participants invest the coins of the blockchain by locking them in the blockchain as a stake. This is efficient since no computational power is needed in mining the coins.
- Proof of Reputation(PoR) - A miner is selected based on his/her reputation in terms of his/her transaction activity, consensus participation, and asset size among other criteria
- Proof of Burn - This is whereby participants 'burn' coins(bitcoins, ether, etc) by sending them to a place where they cannot be retrieved. This shows commitment by the participants, the more coins one burns the higher the chances of being selected to mine the next block in the chain.
- Proof of Capacity(PoC) - In this case, disk space is invested. The more disk space a miner provides, the higher the chances of being selected to mine the next block.
We will discuss these in-depth in later articles.
As transactions are added to a block, those that pay higher fees are prioritized, this depends on the network activity. It is just like in a bank, if there is high traffic, most likely the transaction fees will be high and those who meet the bar receive special attention, this is also common in blockchain networks, when the network is very busy, miners prefer to mine transactions that generate the highest return. This and other criteria are used during mining transactions.
On Bitcoin, blocks are built on top of each other, hence the term 'block height'. As the block height grows, it becomes impossible to change or manipulate any transaction of data.
The higher the block the higher the hash rate difficulty, hence more security on the blockchain. Each block in the chain references its predecessor thereby forming an immutable chain.
Spending a transaction.
After a transaction has been processed using the underlying algorithms, it is added to the distributed. It is also broadcasted to the entire network that this amount X belongs to person A, now participant A can choose to send or spend amount X.
This transaction can be individually verified by all nodes of the blockchain. They all have to validate the transaction, any similar transactions are rejected. Timestamps and account balances are also used among other criteria.
Consider the following chain of transactions between Joe, Alice Bob, and Gopesh.
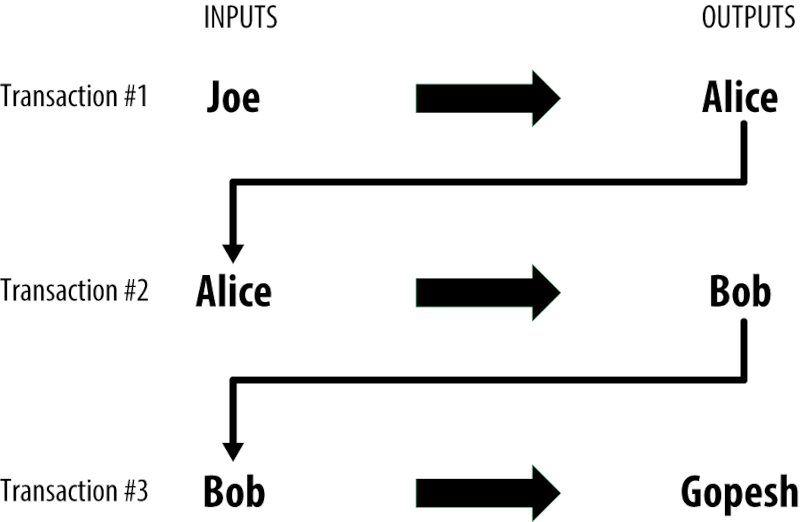
Here we see a chain of how the value was transferred from one party to another. A transaction depends on the outputs of its predecessor.
Double spending.
This is the case whereby digital assets are spent more than once. For example, a participant may purchase an asset using coins, then modifies the transaction in a block making him/her able to spend the same coins in another transaction. This is one of the vulnerabilities that face small blockchains. This is because smaller chains can be centralized.
Miners create blocks that hold transactions. The block is hashed, this hash entails its predecessor's information, a timestamp, and its transactions. After verification using the PoW consensus algorithm and the block gets added to the chain, a new block starts forming, and so on. Now a miner can decide to mine a secret block outpacing a real block's creation. In this case, the miner can decide to modify transactions in the block hence spending previous coins on new transactions.
Preventing double-spending
Bitcoin prevents double-spending as follows. First, when a transaction is received, it is confirmed a maximum of 6 times before it is added to a block. Other similar subsequent transactions are discarded and considered invalid.
Secondly, transactions have timestamps, this makes it very difficult to manipulate or reverse transactions.
A combination of decentralized validation of transactions and timestamps makes it impossible for malicious miners to use a digital asset twice.
Summary
Nodes on the Bitcoin blockchain validate all blockchain transactions using consensus protocols. Mining ensures security for all transactions.
Mining is also responsible for creating new coins, these coins enter circulation as rewards to miners who use their computational resources to maintain the network by hosting bitcoin nodes.
Blockchains prevent double-spending by using a combination of cryptography and decentralized validation of transactions by a PoW consensus mechanism.
References
Mastering Bitcoin - Andreas M. Antonopoulos(Chapter 2)