Open-Source Internship opportunity by OpenGenus for programmers. Apply now.
Reading time: 35 minutes
In this article, we will understand how the Internet works using the ISO OSI model of networking. We will begin by understanding the ISO OSI model which reflects the structure of the different components of the Internet and then, use an example of our URL to understand how everything works together.
Why to use ISO OSI?
We use this model because of the following reason:
Now there are various functions that are undertaken to transfer data successfully from one Host to other Host. Now these functions can be divided in two parts:
1. Mandatory Functions
It is mandatory to define and use these Functions in the model. It involves functions like:
a. Error Control
b.Flow Control
c. Access Control
d. Multiplexing and De-multiplexing
e. Addressing and etc.
2. Optional Function
It is not mandatory to define and use these Functions in the model.The implementation of these functions is optional in the model.
a. Encryption / Decryption
b. Checkpointing (useful while Downloading from internet)
c. Routing (Yes Routing is optional in Networking)
Benefits of ISO-OSI model
Benefits of ISO OSI model are:
- It say that we club together similar functions . Its like a divide and conquer approach is adopted here.
- The varibales and Functions required to implement are protetced in a layer and are not scarttered all over the diffrenet layers. So, it gives a kind of Encapsulation.
- This model says we are only concerned about what a layer does and not how a layer does/implements these . So, it gives a kind of Abstraction.
- The Testing also becomes easy if we adopt this model . As all the models can be tested invidually.
OSI model
There are seven layers in the OSI model namely:
- Application Layer
- Presentation Layer
- Session Layer
- Transport Layer
- Network Layer
- Data link Layer
- Physical Layer
Physical Layer
This layer is more of the physical connections rather than networking (CS) related stuff . This layer deals with how our data, which are in bit are going to be get converted into be various kinds of signals and how these are to be transported among routers and hosts.
It handles the concepts like:
1. Transmission: It gives idea about type of the channels are half-duplex ,simplex, Full duplex.
2. Topology: It gives an idea about topology of the network.( Ring Topology , Bus Topology, Star Topology etc.)
3. Encoding: It gives an idea of what encoding and decoding schems should be used to convert 0’s and 1’s into signals (waves) and send them across the channels.
Data Link Layer
The most important functions implemented in this layer are:
1. Flow Control – The sending rate of data should be in such a way that reciever can recieve the packets without any loss of packets. In simple words, Flow control means the rate at which sender is sending should be somewhat sinked with the rate at which receiver can receive and process the data and If a sink is not maintained then the data packets would get lost.These Flow Control also helps in determining the algorithm in which we will repeat the process of sending the lost packets.
This Layer defines the flow controls methods that are to be used or adopted to ensure proper flow of data across the nodes(from host to reciever) (S&W or GBN or SR).
2. Error Control – Here we take care of the fact that data doesn't get corrupted while transfer , the functions are implemented which help in error detection .Algorithms like CRC and Checksum are used (either of the two algorithms are used in the implementation). The CRC (Cyclic Redundancy Check) algorithm is implemented here to detect the errors (if any might have occured).
Framing – The TCP /UDP packets are framed and sent . The task of this is to put the packets (datagrams from Network layer) received from above layers into a frame and send it. These frames have a SFD(Starting Frame Delimiter) which alert the routers that a new packet is coming.
And these packets can even have a ED (End Delimiter) when we use variable length Frames saying that the packet is over.
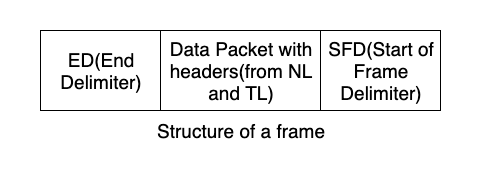
To mark this ED 2 strategies are used:
- Character Stuffing
- Bit Stuffing.
The DLL (Data link Layer) can be further divided into 2 parts:
1. LLC (Logical Link Control) –This layer is Dealing mainly with Flow control and Error Control.
2. MAC (Medium Access control) – This layer deals with Framing, Access Control methods, Error Control (yes it also does), Physical Addressing.
Network Layer
This layer is a important layer but doesn't give acknowledgements when it recieves a packet successfully , this layer deals with the host-to-host connectivity, i.e., this layer is concerned about how packets are to be transferred without error from one host (sender) to other host (receiver). This Network layer uses the Logical Addressing which is unique for a device in the entire internet .
This layer also deals with Switching of the packets to reach the desired host. The Switching of Packets is done by using the Routing Tables.
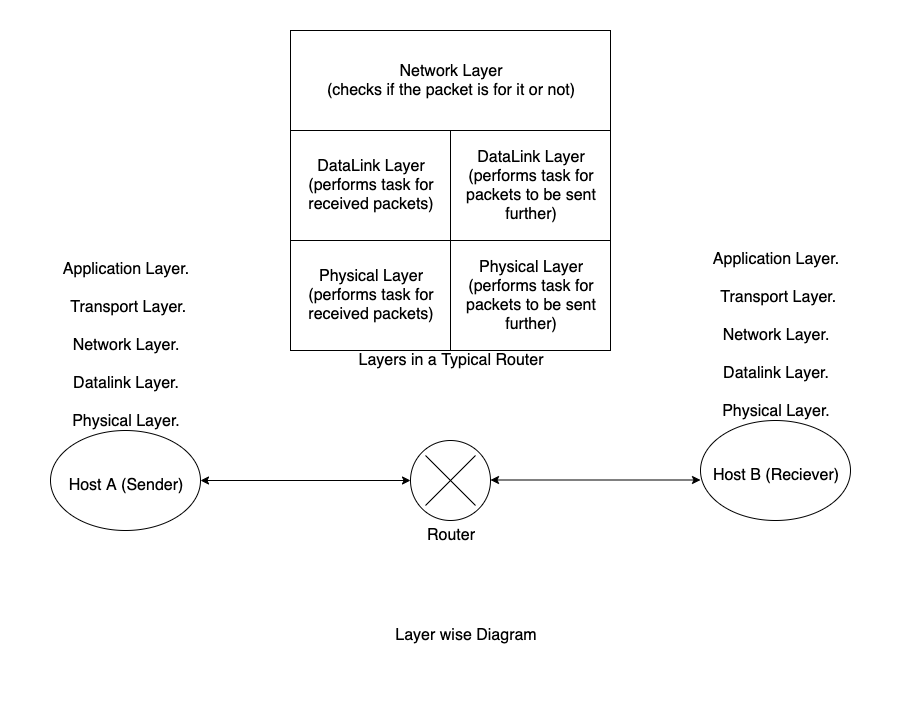
This Layer is also responsible and performs the task of Congestion control.
One more most important that this layer also performs is Fragmentation of packets , the Fragmentation is done , when the packets are to be transferred through a network which have less MTU (Maximum Transmission unit).
Transport Layer
This is final layer responsible for all real stuff , all the rest layer implementation depends upon the application and this Layer handles the End-to-end connectivity it means this layer is important for the data packet to reach the exact port of the host . The Network Layer will bring the packet and give to host but the Transport Layer is the layer that helps the data packets to reach the designated port.
Some other important Functions of Transport layer are Flow Control (using SR protocol), Error Control, Segmentation, Multiplexing and demultiplexing, Congestion control.
Session Layer
This Layer mainly deals with:
- Authentication and Authorisation
- Whether Checkpointing should be used or not.
- Whether Synchronisation be used or not.
- Whether we should use Logical grouping of operations (i.e., either all operations or no operations)
Presentation Layer
In the Presentation Layer, we can find functions implementing:
- The process of Encryption and Decryption
- The Process of Compression
Real Example
Suppose you want to connect to iq.opengenus.org.
So , in the begging we will type this iq.opengenus.org in our url now to find the IP address of iq.opengenus.org using the DNS (Domain Name Server) which will be searched. After that the IP the iq.opengenus.org will be give to us (all these are underlying).
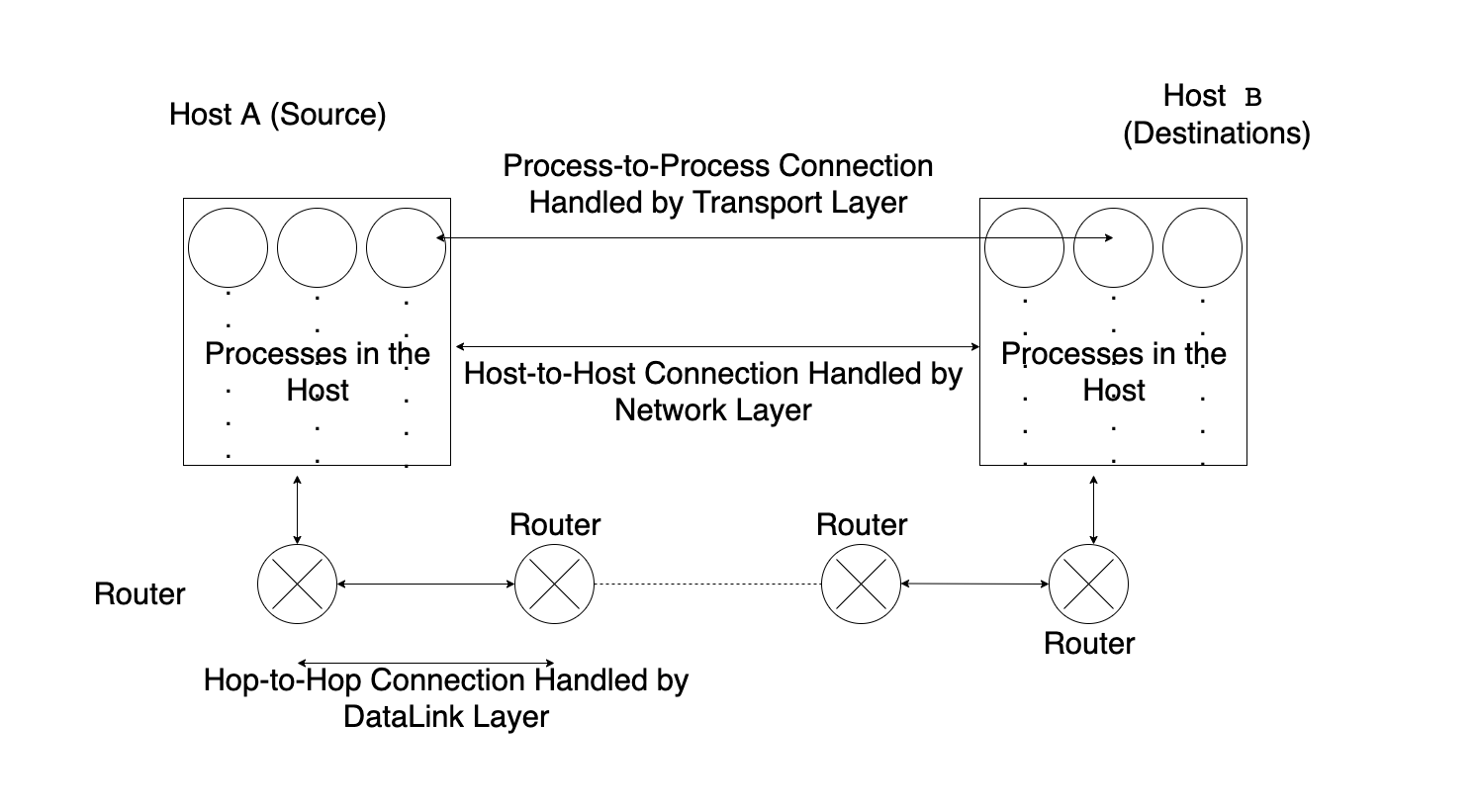
Now the data we want to send to iq.opengenus.org will be given by application layer to Transport Layer . And now the Transport Layer will perform the Segmentation of data (if neccessary) .
The Segmentation is done that the data can go and seat easily in the Frame (will be describing it shortly). The Frame has a certaing size depending on the MTU of the Network. This MTU can be different for different networks. Now after that in Transport Layer Port number are added to the data packets .
So , it can be clearly noted that this layer is responsible for Process-to-Process communtcation among different hosts. Popular port numbers are usually available by default.
Now after that the segment(the data packet) is given to the Network Layer. Here the data packet is known as datagram. Here the IP addresses of the Sender and Reciever are added to the Data Packet. Thus, this layer is responsible for Host-to-Host communication.
In this Layer sometimes even fragmentation of data packets is done if required . It is done so that the data packet can go and easily sit in a frame.
These all datagrams have a unique identification number and if these are futher fragmented . And each of this fragments is findout by using the fragmenation offset.
Point to be noted the fragments will be having a same identification number.
After that the Packet is given to Data Link Layer where the MAC addresses of source and destination are added.
The Datalink Layer is responsible for Hop-to-Hop connection. It means this layer deals with tranfer of packet from host-to-router or router-to-router or router-to-host. This Layer after successfully recieving a packet gives out acknowlegement.
Now an important thing to note is that initially by Logically ANDing the Subnet mask and Destination IP address we try to find to that if we have an entry for the destination network in the router i.e we try to find if the destination is int he same network or not.
If no entry is present in routing table then we use the mac address of the default gateway (router) as the destination mac address. Now to find the MAC address of the router the host sends ARP request so that it receive the MAC address.
ARP (Address Resolution Protocol) request is like saying please send me your MAC address whose IP address is this (Logically).
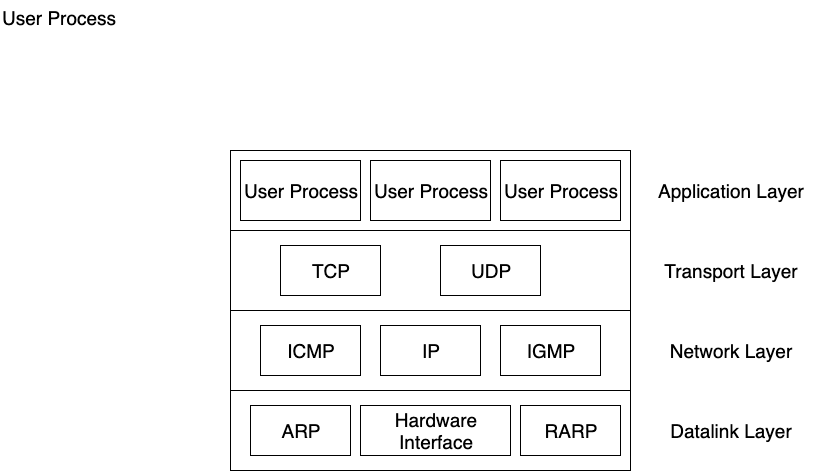
This process in repated in every router unless we reach to the destination network router. After reaching the destination network router the destination Host's MAC address is added to the data packet (by using ARP Protocol). After reaching the destination Host the headers are removed in each going from datalink layer to transport layer. And finally the datapacket reaches the specified process by using the port numbers.
And finally after these successful step the Transport layer gives a acknowledgement to Host that the packet has been successfully delievered.
Difference between Segementation and Fragmenation. Segmentation is done at transport layer(TL) and it done only in the host as routers don't have a TL.
But the Fragmenation is done in the Datalink Layer and it is done in the Routers.
This is how overall our internet works.
