
Open-Source Internship opportunity by OpenGenus for programmers. Apply now.
firewalld is a Linux utility used to manage firewall rules. In this article, we discuss firewall management using firewalld.
Table of contents.
- Introduction.
- Installation.
- Zones.
- Ports.
- Services.
- Creating zones.
- Summary.
- References.
Introduction.
A firewall is a set of rules that define whether traffic is allowed through a system.
iptables and firewalld are tools used to manage firewall rules in Linux.
Installation.
To install firewalld on RHEL, we first update the system:
$ sudo dnf update
Now to install firewalld we write:
$ sudo dnf install firewalld
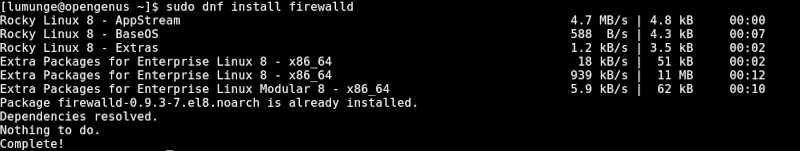
After the installation is successful we start it as follows:
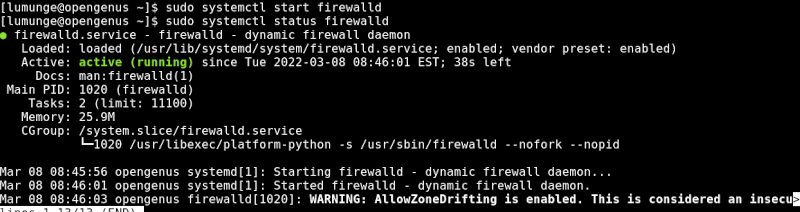
$ sudo systemctl start firewalld
To make this service start at boot time automatically we enable it by writing:
$ sudo systemctl enable firewalld
To make sure the service was started we can check its status:
$ sudo systemctl status firewalld
Zones.
These are where the firewall rules we have declared are applied.
Zones include:
drop: no reply for received packets. Once received they are dropped.
block: In this case, packets are not received at all. They meet an icmp-host-prohibited message.
public: All packets and services are allowed through.
work: This zone is used for work machines that are trusted.
internal: This is similar to the above zone but with a selected type of services or packets that are allowed.
external: Configured for NAT masquerading, therefore we can use it for example, when using the firewall as the gateway. Here the internal network will remain private but it is reachable.
DMZ: We use this zone for demilitarized computers(isolated computers with no access to the internal network). In this case, only specific connections are allowed.
home: It allowed selected incoming connections, mostly used in homes where all computers trust each other.
Trusted: Here, all traffic to the system is allowed through.
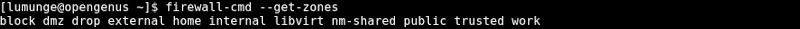
In Linux, we can list firewalld zones by writing:
$ firewall-cmd --get-zones
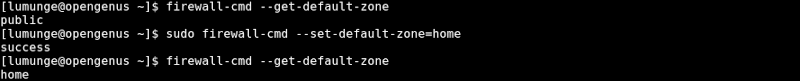
To check the currently used zone, we write:
$ firewall-cmd --get-default-zone

To change the default zone we write:
$ sudo firewall-cmd --set-default-zone=home
An active zone is a zone configured with an interface. To get active zones, we write:
$ firewall-cmd --get-active-zones
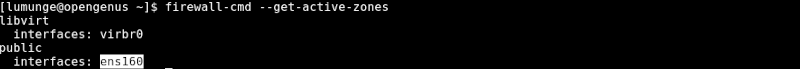
We can also change zones for network interfaces. For example to change the wireless interface zone to the trusted zone we write:
$ firewall-cmd --zone=trusted --change-interface=wlan0
To verify this change we get the active zones as shown previously.
Ports.
A port is a communication endpoint in a computer that another computer uses to communicate with the computer.
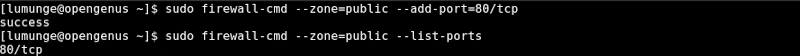
To allow port 80 where HTTP service is, we write:
$ sudo firewall-cmd --zone=public --add-port=80/tcp
To verify this was successful we write:
$ sudo firewall-cmd --zone=public --list-ports
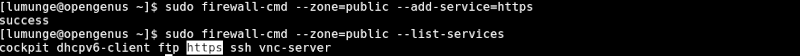
We can also specify the service instead of the port by writing:
$ sudo firewall-cmd --zone=public --add-service=https
We can also specify multiple ports. For example, to open ports from 20 to 25, we write:
$ sudo firewall-cmd --zone=public --add-port=20-25/udp
After applying or removing any rule, we should reload the service so the changes can take effect.
We can close a port by using the --remove-port option:
$ sudo firewall-cmd --zone=public --remove-port=80/tcp
We can also use the service name of the port:
$ sudo firewall-cmd --zone=public --remove-service=hhtp
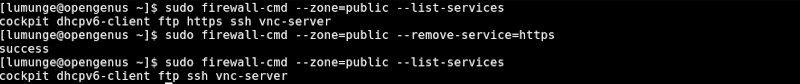
Services
These are a collection of ports that are associated with a single service. This makes it easier to manage multiple ports. For example, ports 20 and 21 are ports for FTP service.
Information concerning services in regards to the firewall is stored in the /usr/lib/firewalld/services directory:
$ ls /usr/lib/firewalld
To list allowed services we write:
$ sudo firewall-cmd --list-services
We can also write:
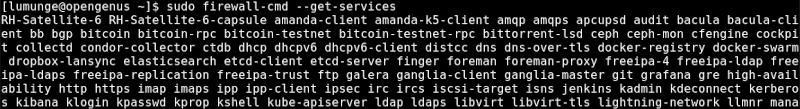
$ firewall-cmd --get-services
For example, we can allow ssh service in the public zone by writing:
$ sudo firewall-cmd --zone=public --add-service=ssh
To verify this action is successful we cal list all services in the public zone:
$ sudo firewall-cmd --zone=public --list-services
This however is temporary, when we reboot, everything is reset. To make these changes permanent we use the --permanent option:
$ sudo firewall-cmd --zone=public --permanent --add-service=http
Creating zones.
Apart from the zones we have seen, we can also define our custom zones.
For example, let's create a firewall zone for the guest in a network.
For this we write:
$ sudo firewall-cmd --permanent --new-zone=GUEST
We verify this by writing:
$ sudo firewall-cmd --get-zones
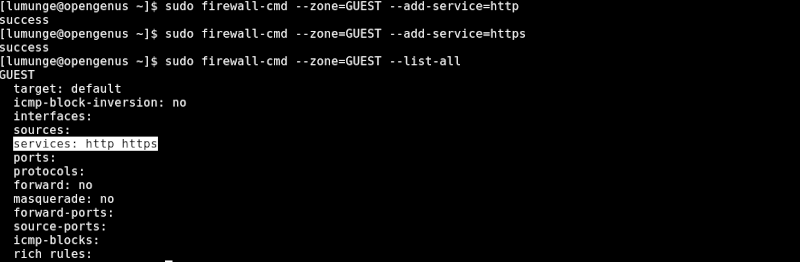
Now, to allow HTTP and HTTPS traffic for the GUEST we create a rule as follows:
$ sudo firewall-cmd --zone=GUEST --add-service=http
$ sudo firewall-cmd --zone=GUEST --add-service=https
We confirm this by writing:
$ sudo firewall-cmd --zone=GUEST --list-all
Now to change the interface to test these changes:
$ sudo firewall-cmd --zone=GUEST --change-interface=[interface name]
After this we can reload the service for the changes to take effect:
$ sudo systemctl reload firewalld
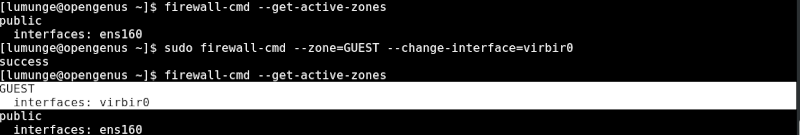
Now to list all active zones we have:
$ firewall-cmd --get-active-zones
At times we may want to perform an action that requires us to allow traffic in all traffic in temporarily. For this we can stop the service by writing:
$ sudo systemctl stop firewalld
To disable it permanently we write:
sudo systemctl disable firewalld
Summary.
We have learned about firewalld command and how it is used in firewall management in Linux. We also learned about zones and their different types, how to allow ports and services and disallow them through the firewall, and created a zone as an example.
References.
We can execute the command $ man firewalld for the command's manual.
