
Open-Source Internship opportunity by OpenGenus for programmers. Apply now.
We use iptables to create firewall rules. In this article, we learn about iptables and how to manage firewall rules in Linux.
Table of contents.
- Introduction.
- Installing iptables.
- Syntax.
- Commands
- An example.
- Summary.
- References.
Introduction.
iptables are programs used by systems administrators to define firewall rules in Linux.
A rule is a condition we specify to match a packet.
We can use them to block or allow traffic through a firewall.
This information is stored in tables, these tables have rules referred to as chains.
Built-in chains in Linux are:
INPUT: these rules control the packets received by the server.
OUTPUT: defines rules that control packets for outbound traffic.
FORWARD: defines rules that control packets through the server.
PREROUTING: It assigns packets as soon as they are received by the server.
POSTROUTING: defines rules that allow us to make changes to packets after they leave the output chain.
A TARGET is an action we specify that will apply when a packet matches a rule we have defined.
A POLICY is the default action taken if no rule matches.
Different types of Iptables are:
Filtering, these will be used to filter incoming and outgoing packets. They have input chains such as INPUT, OUTPUT, FORWARD.
NAT(Network Access Translation), this table stores rule that handles the routing of packets to networks that are not directly accessible. Its chains are PREROUTING, OUTPUT, and POSTROUTING.
Mangle, this is used for specialized packet altering e.g, adjusting the IP header for packets. It has all chains.
Raw, we use it for exempting packets from connection tracking. Its chains include PREROUTING and OUTPUT.
security, these tables to define rules for mandatory access control Its chains are, INPUT, OUTPUT, FORWARD.
Installation iptables.
To get started we will update the system and install the iptables package:
$ sudo apt-get update && sudo apt-get upgrade
Now to install iptables:
$ sudo apt-get install iptables
Note that, if we want to preserve iptables rules that we have defined even when the system reboots we install the iptables-persistent package:
$ sudo apt-get install iptables-persistent
We can also save changes so the rules are preserved by writing:
$ sudo /sbin/iptables-save
or
$ sudo iptables-save
Syntax.
To write iptables commands we use the format shown below
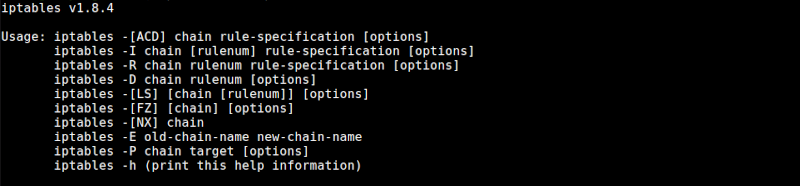
Commonly used options are;
- -A which we use to add a rule to a chain.
- -C, to check for a rule matching a chain.
- -D, to remove rules from the chain.
- -F, to flush/remove all rules.
- -I, to add a rule at a specific position in the chain.
- -L, to print out all rules from a chain.
- -N, to create a new chain.
- -v to print output while working.
Commands.
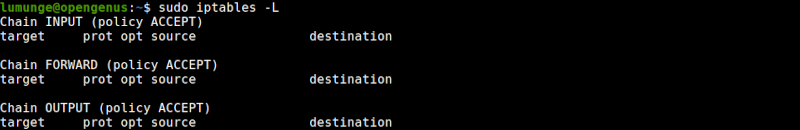
To check the current status of the tables we write:
$ sudo iptables -L
Creating rules.
Let's create a rule that allows traffic from our own host localhost:
$ sudo iptables -A INPUT -i lo -j ACCEPT
lo stands for localhost and -i specifies the interface.
We can also control traffic using the IP addresses of host machines. For example to allow traffic only from a specific host we write:
$ sudo iptables -A INPUT -s [HOST-IP] -j ACCEPT
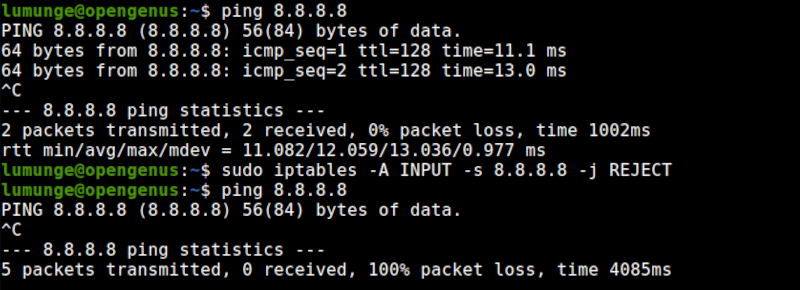
And to reject packets from a host we write:
$ sudo iptables -A INPUT -s [host IP] -j REJECT
An example;
We can also specify a range of IP addresses, for example, to allow traffic from 20 IP addresses, 10.16.3.75 - 10.16.3.95 we write:
$ sudo iptables -A INPUT -m iprange --src-range 10.16.3.75-10.16.3.95 -j ACCEPT
Dropping packets.
Dropping packets is whereby when packets are received the host doesn't send back a reply. The packets are dropped. To DROP incoming packets, we write:
$ sudo iptables -P INPUT DROP
To undo this, we write:
$ sudo iptables -P OUTPUT ACCEPT
An example;
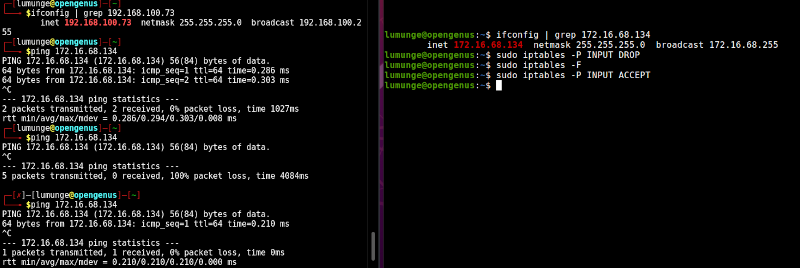
We can also specify which ports can have traffic through them. For example to drop traffic from port 69 for TFPT service we write:
$ sudo iptables -A INPUT -p tcp --dport 22 -j DROP
Deleting rules.
To remove a rule we no longer need from the iptables we use the -D option:
For example, to remove a rule, we first list all the rules so we are sure:
$ sudo iptables -L --line-number
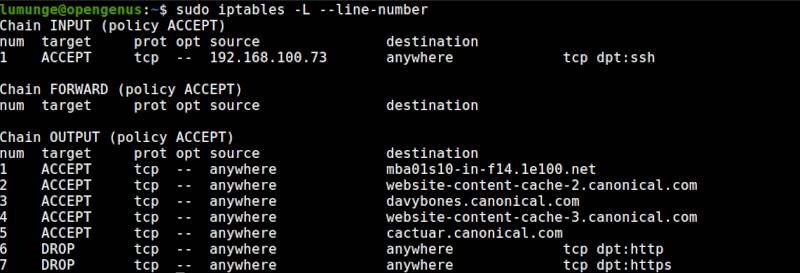
Then to remove the rule from the OUTPUT chain we write:
$ sudo iptables -D OUTPUT [number]
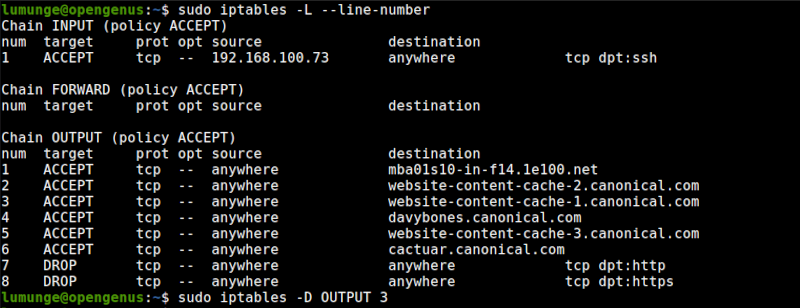
To remove all rules we use the flush option:
$ sudo iptables -F
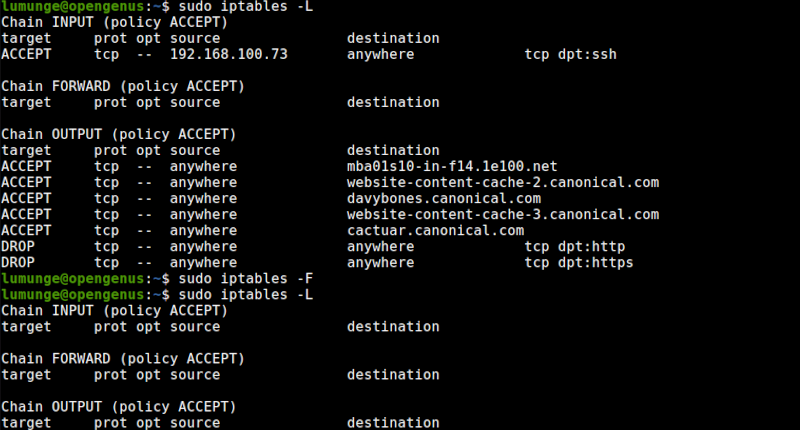
To restore an iptables configuration we write:
$ sudo iptables-restore
An example.
We have a host. It cannot be accessed except via ssh and only using a single specific host. We also want this machine to update itself automatically and access a specific number of company domains.
For this we have to apply the following rules/commands:
- We have two company domains we need to allow this host to access. For this we use the command:
$ iptables -A OUTPUT -p tcp -d [domain.com] -j ACCEPT
A means that we are adding, the rule will become part of the OUTPUT chain. We use -p option followed by tcp to mean that the rule applies for tcp packets, the -d option if followed by the destination.
The action is to ACCEPT which we have specified and is preceded by the -j option.
Now to block access to other domains, we have to create two rules to DROP traffic on HTTP and HTTPS ports 80 and 443:
$ iptables -A OUTPUT -p tcp --dport 80 -j DROP
$ iptables -A OUTPUT -p tcp --dport 80 -j DROP
Now to create a rule to allow us to be able to access the machine via ssh port 22 using IP address 192.168.100.73:
$ iptables -A INPUT -p tcp -s 192.168.100.73 --dport 22 -j ACCEPT
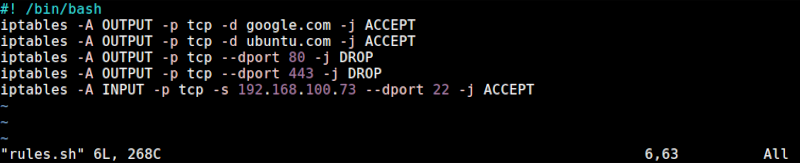
Now to put all this in a script:
#!/bin/bash
iptables -A OUTPUT -p tcp -d google.com -j ACCEPT
iptables -A OUTPUT -p tcp -d ubuntu.com -j ACCEPT
iptables -A OUTPUT -p tcp --dport 80 -j DROP
iptables -A OUTPUT -p tcp --dport 443 -j DROP
iptables -A INPUT -p tcp -s 192.168.100.73 --dport 22 -j ACCEPT
First, we change the permissions of the script to execute it:
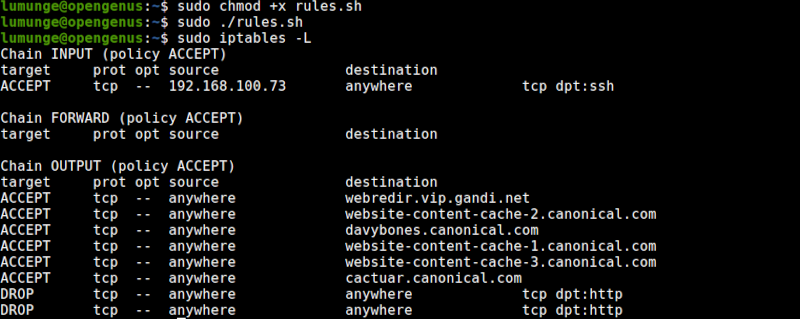
If the execution was successful our tables should look as shown above.
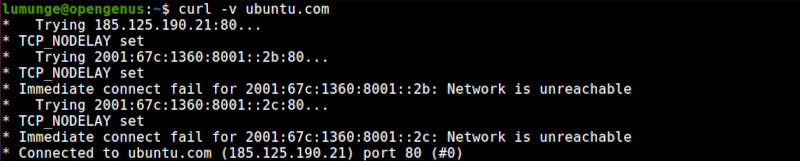
Now if we try to reach google using, it can be reached however, when we try to reach another different domain, it will be unreachable since we have not specified a rule.
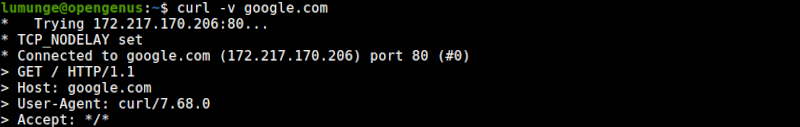
If fails to reach yahoo.com
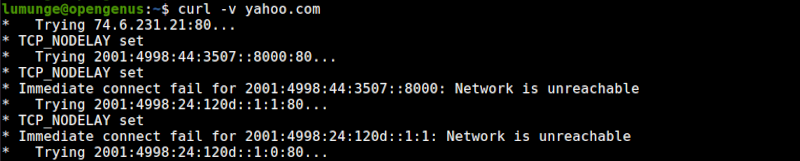
We can also reach ubuntu for automatic updates
Summary.
We have learned about iptables, chains, and how to use the iptables command to manage firewall rules in Linux.
References.
We can execute the command: $ man iptables for the command's manual.
