
Open-Source Internship opportunity by OpenGenus for programmers. Apply now.
We have explored the System Design of a Firewall along with the basics of Firewall and a sample Firewall Design in a real system.
Table of content:
- What are Firewalls?
- Uses of firewalls
- Types of Firewall
- System Design of a firewall
- Sample firewall architecture
We will get started with System Design of a Firewall now.
What are Firewalls?
A firewall is a security device that monitors incoming and outgoing network traffic and based on a set of security rules decides whether to allow or block specific traffic.
Firewalls have been the first line of defense in network security for many years , it sets up a barrier between the internal network and the incoming traffic from external sources in order to block malicious traffics like viruses , malwares and attackers.
Uses of firewalls
Uses of firewalls are:
- Prevents passage of unwanted content
- Stop Unauthorized access
- Guarantees Security Based on Protocol and IP Address
- Makes Online Gaming Safer
- Protects Operations in Enterprises
We will dive into the use-cases further.
- Prevents passage of unwanted content
There is a lot of bad and unwanted content over the internet. These contents can easily penetrate the system unless a strong firewall is in place. Most operating systems have a firewall that effectively take care of undesired and malignant content from the internet.
- Stop Unauthorized access
A firewall prevents any sort of possibility of an unethical hacker from obtaining remote access into a system or server. Such type of remote access is unauthorized and can be used for destructive purposes too.
A strong firewall is required to protect the users data, transactions, etc. It is required so that users are not compromised by outside attackers and attacks are blocked
- Guarantees Security Based on Protocol and IP Address
The hardware firewalls are useful for examining traffic activities based on a certain protocols. Whenever a connection gets established, right from the beginning to the end, activities are tracked to keep the system protected.
Network Address Translation (NAT) is a type of firewall that protects systems from those which are outside the network . As a result, these systems IP address is visible only in their network. This helps in keeping them separated and safe.
- Makes Online Gaming Safer
Online gaming is one of the most popular internet activities, but it also comes with a potential security risks. There are various malwares targeted towards online gamers, existing on unsecured or recently compromised game servers.
In majority of the cases, the firewalls manage their configuration themselves based on the requirements of the game, using information provided in metadata to block malicious activities by malicious games.
- Protects Operations in Enterprises
Companies rely heavily on enterprise software and systems. Decentralized distribution systems, along with the ease of accessibility of data , is enables authorized developers or company administrators to use and work on the data for business needs.
A user can log in to his system from any system within the network. However, given such a vast network system and huge data, having a strong firewall in place is of atmost necessity, and the firewall is the most important component in imparting security to all these aspects. Without effective firewalls, it would be very difficult for organizations to have such seamless operations, and the activities would be badly hampered.
Types of Firewall
Types of Firewall are:
- Packet Filtering
- Proxy Firewalls
- NAT firewalls
- Web Application Firewalls
- Cloud Firewalls
We will dive deeper into the types of Firewall.
- Packet Filtering
These are the most basic firewall type, packets are examined and prevented from moving on if specific security rules is not met. The firewall performs a checks on the packets arriving from the network routers and inspect specifics like source and destination IP address, port number, protocol, and other data.
However they do not open the packet to verify and check the contents within the packets.
The packet filtering firewalls can be stateful or stateless. Stateless firewalls only analyze each packet individually, while stateful firewalls which is the more secure option take previously inspected packets into consideration.
- Proxy Firewalls
They are also known as application level firewalls , they filter traffic at the application layer of the OSI network model. Proxy firewalls monitor traffic at the application layer (which includes HTTP , FTP protocols at this layer) to detect malicious traffic ,both stateful and deep packet inspection are used.
Proxy firewalls are usually in the cloud or through another proxy device. Instead of allowing traffic to connect directly, a connection to the traffic source is established and the data packet is inspected.
- NAT firewalls
Network address translation (NAT) firewalls work by assigning a public address to a group of devices inside a private network. With NAT, individual IP addresses are hidden. Attackers scanning for IP addresses on a network to target a victim are prevented from discovering specific details.
NAT firewalls and proxy firewalls connect groups of devices with the outside network. They can be very useful to setup borderlines between networks.
- Web Application Firewalls
Web application firewalls filter, monitor, and block data packets as they come in and out of websites or web applications. A web application firewall is setup either on the network, at the host or in the cloud and is usually placed in front of one or many websites or applications to provide security.
The functioning of web applications firewalls are similar to the proxy firewall, but they are more specifically focused on defending against application layer web-based attackers.
- Cloud Firewalls
When a firewall is designed using a cloud solution, it is known as a cloud firewall or FaaS (firewall-as-service). Cloud firewalls are maintained and run by the cloud service providers.
The biggest advantage of cloud firewalls are the scalability they provide end users based on the organizations demand or traffic load.
System Design of a firewall
To design a firewall four basic guidelines can be used
- Developing a security policy.
- Creating a simple design solution.
- Using devices as they were intended.
- Implementing a layered defense to provide extra protection.
Developing security policy
The first step to design a firewall system is to create a security policy. The policy should define acceptable and unacceptable behavior, should state restrictions to resources, and should adhere to the organizations business plan and policies. Without a security policy, it is impossible to develop a security solution that will meet the organizations needs.
A policy defines who is allowed to access resources, what they are allowed to do with resources, how resources should be protected, and what actions are taken when a security issue occurs.
Creating simple design solution
The firewall system design should be kept simple and should follow the security policies. Simpler the design is, easier it is to implement it, maintain it, test and troubleshoot it, and adapt it to new changes.
Using devices
To provide network and application security appropriate security devices have to be used and configured. Network devices have functional purposes, they were built with a specific purpose in mind.
Security devices can be used to protect the organizations appliations and filter out traffic. The devices themselves have specific Ip address and mac address and come configured with filtering and monitoring rules.
Implementing layered defense
A security design uses layered defense approach. It means that usually only one layer of defense is not used protect network. If this one layer is compromised, the entire network will be exposed.
Organizations make use of multilayer defense in the firewall system design. With multiple layers, if one layer is compromised, we still have other layers behind it protecting the system.
This is advantageous as the attacker has to penetrate through multiple layers to reach the application and cause damage to it.
Sample firewall architecture
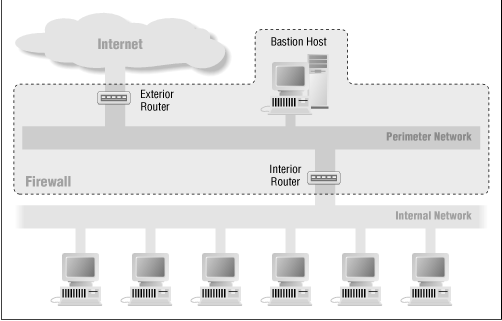
This is the screened subnet architecture which is one of the most common firewall architecture.
There are multiple components within this architecture
Exterior Router
This is to route data packets from the exterior internet to the organisations internal network. The job of a router is to develop connections and assists in transporting data packets between different networks.
The exterior router connects the companys interior gateway and the internet gateway.
Host
This is the main point of contact of the site from the outside world.
Internal Router
This router is only for the internal network of the organisation. It protects the internal network from the outside world.
Perimeter Network
The perimeter network acts as main isolation agent between the internal network and outside world.
Routing and Packet Filtering Rules
Interior Router
- Rule for outgoing Telnet and FTP connections. This is required as telnet and ftp can be used to connect to the exterior internet.
- SMTP incoming and outgoing rules which is used for sending and receiving mails between outside world and internal services.
- Internal DNS rules , which include lookup in dns, query internal dns for internal services and external dns for other services.
- Default rules to block spoof attacks.
Exterior Router
- Rule for outgoing Telnet and FTP connections.
- SMTP incoming and outgoing rules which similar to interior router rules is used sending and receiving mails but between host and outside world.
- DNS rules , which include lookup in dns, query only external dns for services and hosts.
- Default rules to block ddos attacks.
Further Additions Possible in the architecture
- Demilitarized Zone(DMZ) - this acts as a perimeter network which protects an organisations LAN
- NAT Gateway - Network Address Translation which allows services in a private subnet in a VPC connect to outside services but not vice versa.
- Intrusion Detection Systems - These are agents present which detect network or malware attacks and prevent them.
With these article at OpenGenus, you must have the complete idea of System Design of Firewall.
