Open-Source Internship opportunity by OpenGenus for programmers. Apply now.
Reading time: 10 minutes
DNS (Domain Name System) Amplification is a form of reflection based DDoS attack, in which a hacker spoofs the look-up requests to spoof the DNS servers to hide the source of an exploit and also to direct the response to the target. The attack exploits the disparity in the bandwidth consumption between the hacker and the targeted web resource. The hacker leverages the functionality of DNS resolvers to flood the victim with malicious traffic in this attack. The attack can also crash the victim infrastructure.
Procedure For The Attack
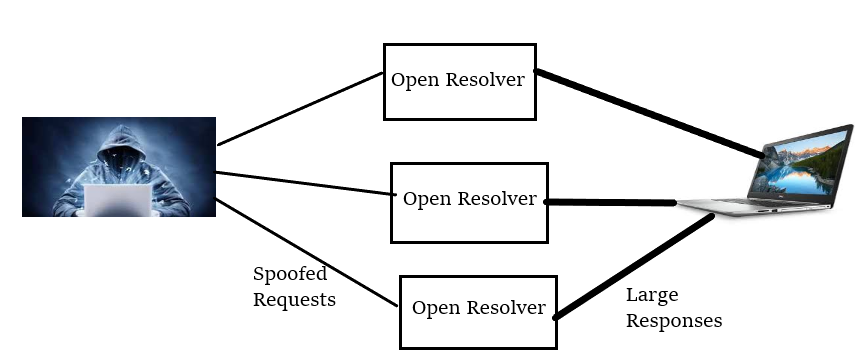
- The hacker initially, uses a compromised endpoint to send the UDP packets with spoofed IP Addresses to a DNS recursor, which points to real IP of the victim.
- After this the UDP packet makes a request to a DNS resolver, often passing an argument such as "ANY" to receive the largest response possible.
- As soon as the DNS resolver receives the request, it sends the large response to the spoofed IP Addresses.
- Finally, the IP Address of the victim receives the responses which flood the victim's infrastructure with huge traffic resulting in the denial of service attack.
Image For Understanding The Attack
Mitigation For The Attack
To stay safe from this attack, follow the following:
- Use ingress filtering (a form of packet filtering) to block all packets coming from outside the network as a fake IP
- Block the specific DNS servers or all open recursive relay servers
- Limit the rate of the total number of open DNS resolvers to avoid the attack.
MCQ Round
Question 1
What is Full Form of DNS?
Domain Name System
Domain Name Server
Destinantion Name System
Destinantion Name Server
Question 2
Which type of attack DNS Amplification is?
DOM Based
Reflection Based
Store Based
Null Based