Open-Source Internship opportunity by OpenGenus for programmers. Apply now.
Reading time: 10 minutes
MAC (Media Access Control) Flooding is a type of cyber attack done in a network to compromise the security of the network switches. In this attack the network is flooded with the fake MAC addresses. The hacker uses this attack to steal sensitive data that is being transferred in the network. The attack is used for forcing the legitimate MAC table contents out of the switch and forcing the unicast flooding behavior for potentially sending sensitive information to portions of the network where it is not normally intended to go.
Procedure For The Attack
- In this attack, the hacker first connects to the switch ports and floods it's interface by forcing legitimate MAC addresses out of the MAC address table through very large number of fake MAC addresses .
- Once the MAC address table is full, the network switch enters into the fail-open mode and behaves like a network hub, broadcasting all the packets on all the switch ports.
- The hacker finally uses an packet analyzer to capture these packets to steal the sensitive information.
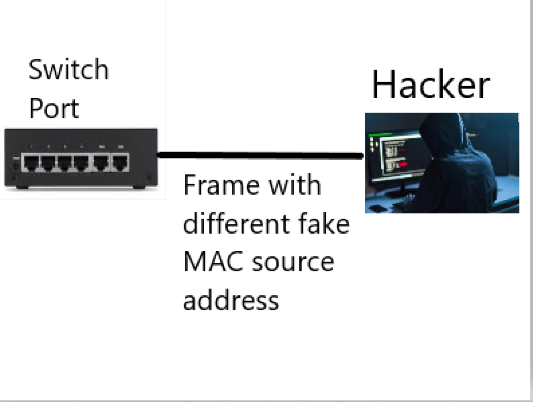
Image For Understanding The Attack
Mitigation For The Attack
To stay safe from this attack, follow the following:
- Authentication, Authorization, and Accounting Servers (AAA) can be used for authentication against MAC addresses as an preventive measures
- Configure the switches to limit the number of MAC addresses on the ports that are connected to the end stations.
MCQ Round
Question 1
What is Full Form of MAC?
Media Access Condition
Media Access Control
Meditek Access Control
Media Accounting Control
Question 2
What does AAA stands out for?
Authentication, Authorization, and Accessbility
Authentication, Authorization, and Accounting
Authentic, Authorization, and Accounting
Authentication, Authorize, and Accounting