Open-Source Internship opportunity by OpenGenus for programmers. Apply now.
Reading time: 12 minutes
Distributed Denial Of Service (DDoS) is a form of cyber attack which is done to make target online services unavailable to the users. The attack disrupts the normal traffic of a targeted server, network or service by overwhelming the target or its surrounding infrastructure. The attack makes the legitimate services inaccessible to the users and can result in the crash of the target server or its infrastructure.
Types
DDoS Attack can be divided into three types:
-
Protocol Attacks: These attacks are also known as state-exhaustion attacks. The attack basically consumes the actual server resources or disrupts the intermediate communication equipment such as load balancer and firewall. The magnitude for this attack is measured in packets per second (Pps). Syn Flood is an example of the protocol attack.
-
Volume Based Attacks: The attack basically is done to consume all the available bandwidth of the victim website. The magnitude for this attack is measured in bits per second (Bps). DNS Amplification is an example of this type of attack.
-
Application Layer Attacks: The attack is basically done to exhaust all the resources of the victim. The attacks target the layer where the web pages are generated on the server and are delivered in the response to HTTP requests. The magnitude for this attack is measured in Requests per second (Rps). HTTP Flood is an example of this type of attack.
Procedure For The Attack
Attack Procedure is as follows:
-
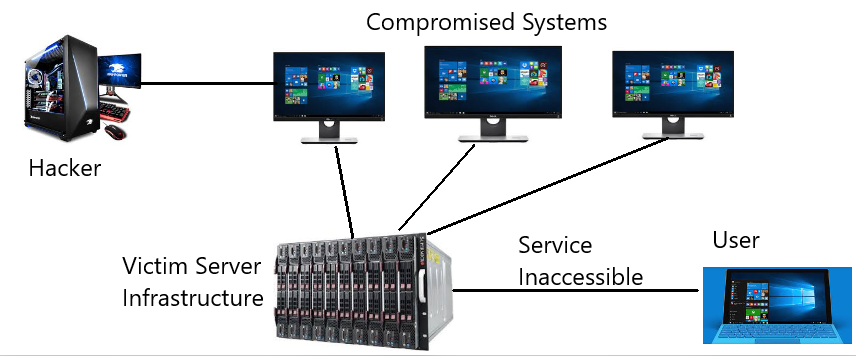
In this attack, a hacker first searches for the target on which he wants to attack. For example, www.ecommerce.com is a website where he wants to attack and wants to make its service inaccessible to its users and also wants to crash the system.
-
Now the hacker requires to gain control of the target networks online machines in order to carry out this attack. For this, the attacker distributes the malware to several devices wherever possible through various methods of social engineering. The devices are compromised in order to turn them into bots (or zombie).
-
Finally, the hacker has control of all the compromised devices and now he uses all these devices as a single entity we can term it as a bot and redirect all the devices traffic to the victim infrastructure and its servers so that the victim system crashes and its services become inaccessible. According to our example, www.ecommerce.com become inaccessible to its users.
Mitigation For The Attack
The WAF(Web Application Firewall) can help to mitigate this kind of attack. One solution that all network admins can apply is to create a blackhole route to redirect the malicious traffic into that route which helps to avoid this type of attack. Update the anti-malware software and firewalls time to time. Organizations should have a modern and up-to-date security infrastructure for preventing this type of attack.