Open-Source Internship opportunity by OpenGenus for programmers. Apply now.
Reading time: 15 minutes
Man In The Middle (MitM) is a type of cyber attack in which a hacker intercepts the communication between two people either to eavesdrop or to impersonate one of the person. The aim of the attack is to steal financial details such as account details, credit card numbers or sensitive details such as log in and password information of social websites.
Procedure to do Man in the Middle attack
Mitm Attack can be done in two ways:
- Passive attack
- Active attack
Passive Attack: In this type of MitM attack a hacker only eavesdrop between the communication, he doesn't actually tamper any data.
Active Attack: In this type of MitM attack a hacker tampers the data between the communication.
Procedure For The Attack
Let's understand the procedure with the help of an example:
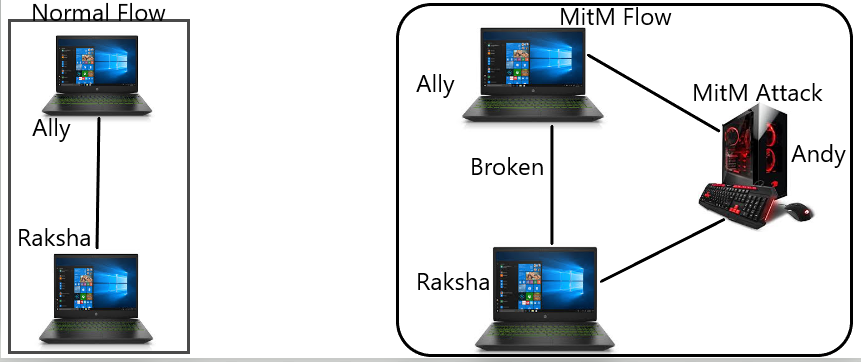
Ally - First Person
Raksha - Second Person
Andy - Hacker
These three works in the same company.
- Ally sent an email to Raksha asking her details for registering her into the company as she is new in the company. Now, Andy is a bad guy who wants to use this details for the wrong purpose.
- Andy uses some open publically available intercept tools such as Ettercap and tries to intercept in the communication. When he succeeds, he tampers the email sent to Raksha in the middle and done some changes such as asking her financial details also for giving her salary every month.
- Now here Raksha doesn't know and she simply replies and gives every detail that has been asked in the email.
- Now before the email reaches to Ally, Andy take all the financial details he needed and remove those and then sent to Ally. So Ally think that she have got all the information that she asked for.
- At the end, Raksha and Ally they both don't know anything about this attack and just done what their duty is but Andy has done the MitM attack and have taken the extra details that have not been really asked. Now he uses this information for the malicious purpose.
Mitigation For The Attack
Never share any credentials or even do the financial related work on the public wifi. Use the best VPN for communicating so that no one can intercept between the communication. Avoid connecting to the Wifi connections that aren't password protected. For website operators, use TLS and HTTPS protocols so that all data is transmitted encrypted.