Open-Source Internship opportunity by OpenGenus for programmers. Apply now.
Reading time: 10 minutes
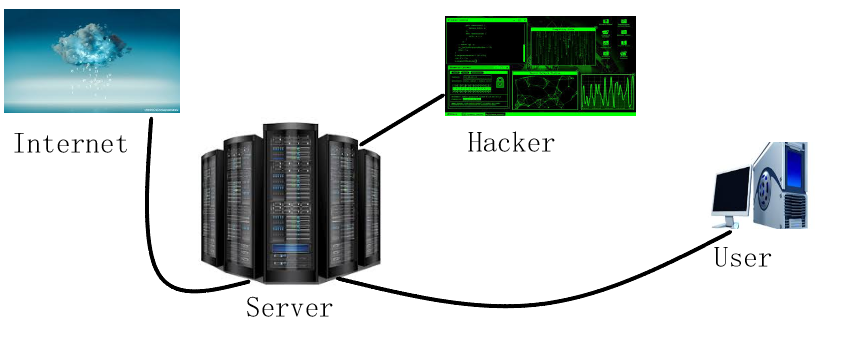
IP (Internet Protocol) Spoofing is a form of cyber attack in which hacker crafts the IP packets which are used to carry out the DDoS attacks as well as MitM attack. In this attack, the fake crafted IP packets are used to impersonate another system or is used to hide the identity of the hacker. The attack provides the hacker an ability to bypass the security scripts, devices, and services that are using the blacklisting method to filter out the IP addresses of known sources of malicious traffic.
Procedure For The Attack
- In this attack, initially, the hacker crafts the malicious IP Addresses by doing modification in the source IP addresses and for this the hacker first search for the IP address which he wants to target through various network discovery tool.
- Now, these modified source IP addresses are treated as a trusted source by the destination address. As this attack is carried out at the network level, there are no external signs of tampering.
- The hacker then carries out the attack with these spoofed IP addresses to flood the victim servers with the large volume of packets to make the victim service inaccessible turning the attack into the DoS attack for the legitimate users.
Image For Understanding The Attack
Mitigation For The Attack
To stay safe from this attack, follow the following:
- Use ingress filtering (a form of packet filtering) to block all packets coming from outside the network, with a (fake) source address inside the network.
- Using a reliable a network attack blocker can help reduce such attacks.
- Organizations may also implement egress filtering to block all the outgoing packets from inside the network with an invalid source address.
- Configure the routers and firewall to reject the packets with private IP Addresses that originate from outside the enterprise perimeter.
MCQ Round
Question 1
What is Full Form of IP?
Internet Protocol
Ingress Protocol
Internet Provision
Ingress Provision
Question 2
Which filtering can be used for mitigating this attack?
Egress Filtering
Ingress Filtering
Xmas Filtering
Null Filtering