
Open-Source Internship opportunity by OpenGenus for programmers. Apply now.
Secure boot is a security standard implemented in the advanced UEFI to prevent malware from attacking the computer during bootup when the computer is most vulnerable.
Table of contents.
- Introduction.
- How it works.
- Enabling and disabling secure boot.
- Summary.
- References.
Introduction.
UEFI(Unified Extensible Firmware Interface) specifies the interface between the operating system and other computer firmware.
Among the features of UEFI, secure boot is among those that make UEFI preferable over Legacy BIOS.
A computer is vulnerable during start-up therefore malware can be installed into the system at this time and go unnoticed.
Secure boot is a mechanism that ensures that the code executed by UEFI firmware is trusted by the Original Equipment Manufacturers(OEM). It protects the computer against malware that is loaded when it boots up so as not to infect the operating system.
How it works.
Assuming there was no secure boot, during start-up legacy BIOS checks the hardware then attempts to boot any software. On Windows PCs, the windows boot loader loads the Windows operating system which takes over to complete the bootup process, on Linux machines the BIOS locates the GRUB boot loader which completes the startup process.
Rootkit malware can be installed in the place of the boot loader and therefore could load the OS except in this case it will be working in the background without a user noticing anything wrong since it stays undetectable. This is because BIOS cannot determine if a specific software or firmware is the boot loader or not therefore it hands over control blindly.
To solve this, secure boot was implemented in the new UEFI. It uses cryptographic checksums and signatures whereby each program that is loaded has a digital signature and a checksum so before the firmware executes a program it first verifies that the program is trusted. This is done by validating the signature and the checksum of a program, if valid, the firmware hands over control to the operating system
This process will stop any unauthenticated code from running in the UEFI firmware thus keeping the operating system safe.
The reason why it is difficult to install another operating system in a windows manufactured machine is because of secure boot. Most x86 hardware from windows manufacturers come pre-loaded with Microsoft keys meaning that the firmware installed on such systems only trusts binaries signed by the same entity - Microsoft.
What does this mean for Linux distros? Microsoft offers a way for Linux distributions such as Ubuntu or Fedora to boot normally on any modern PC including when secure boot is enabled.
This is because Linux distros have a shim signed - this is a boot loader that boots the GRUB boot loader on many Linux distributions after which the booting process proceeds normally.
Enabling and disabling secure boot.
It is possible to control secure boot from the computer's UEFI interface. This process will be different for different machines and operating systems.
Here we list the process for a Windows 10 OS which is also applicable to 8 or 8.1.
-
First we have to access the BIOS settings. We can either power off the machine and press a keyboard interrupt key to enter the UEFI or we could hold the shift key and restart the machine using the restart button.
-
The next step if we used the second option from above is to select troubleshoot -> Advanced options -> UEFI firmware settings which will takes us right to UEFI BIOS settings.
-
As we mentioned earlier, different computers have different firmware therefore the secure boot option is either in the boot, security, system configuration or authentication tabs.
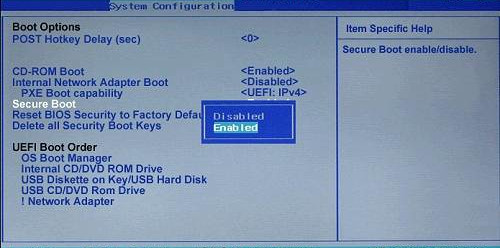
- Disabling or enabling involves toggling between the two options.
Apart from changing secure boot, we can also control the signed certificates secure boot offers by removing existing ones and adding new ones.
For example, we can remove Microsoft's certificates and install our custom certificate meaning that a specific PC will only boot bootloaders that are compiled and signed by us.
Summary.
Secure boot is a measure to protect malware executing during the boot process.
Microsoft acts as a certification authority in that it signs programs on behalf of other organizations so the programs may run. There are specified requirements an organization has to meet including their code being audited for it to be allowed to run.
Users can also remove platform-provided keys and enroll their own keys.
