Open-Source Internship opportunity by OpenGenus for programmers. Apply now.
Reading time: 16 minutes
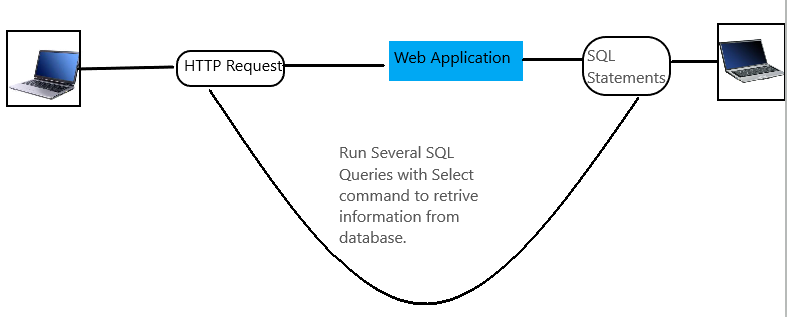
SQL(Structured Query Language) Attack is a cyber attack used for the manipulation of the backend database through the malicious SQL Query. The attack allows a hacker to cause repudiation issues and spoof the identity. The attack also allows the complete exposure of the database which later can be used for the malicious purpose. The hacker if wanted can even destroy the data or do modification in the database.
Procedure For The Attack
Attack Procedure is as follows:
-
Hacker first searches for the website in which the parameter of HTML are not properly validated (i.e. tags are not closed etc.) by running malicious SQL queries on the website.
-
While running the queries if error related to SQL is displayed on the webpage. This gives the hint to the hacker that the page is vulnerable and he then ran further queries on the website.
-
He further finds the version number of the database and according to that the hacker applies the attack and run the queries and tries to retrieve the database and the information inside it.
-
The hacker then uses this information for the malicious activity such as cyberbullying, sending spam emails etc.
Types Of SQL Injection
There are mainly three types of SQL injection:
Union Based SQL Injection
- Union Based SQL Injection: In this type of SQL Injection Attack, the hacker uses Union statement to integrate two or more SQL commands to retrieve the data from the database.
Blind SQL Injection
- Blind SQL Injection: In this type of SQL Injection Attack, the hacker extracts the data by asking the questions to the database.
Error Based SQL Injection
- Error Based SQL Injection: In this type of SQL Injection Attack, the hacker tries to cause an error in the application in order to extract the data from the database. The attack only works on MS-SQL Server.
Mitigation For The Attack
The attack can be prevented by properly validating the user-supplied input in the proper fields such as expected data types. In order to mitigate the attack ensure the proper design of the application. Also, use proper stored procedures and parameterized queries to avoid the attack. Don’t leave any sensitive data in the plaintext and applyv proper encryption algorithm on the data.
Demo Of The SQL Injection
First the hacker check for the error
http://www.demo[.]com/faculty/profile.php?id=1' -- -
If error is shown then the hacker try to find out the tables.
http://www.demo[.]com/faculty/profile.php?id=96'union select table_name,2,3,4,5,6,7,8 from information_schema.tables-- -
After this the hacker then tries to find all the table name in a single time only and for that he uses group concat function.
http://www.demo[.]com/faculty/profile.php?id=96' union select group_concat(table_name),2,3,4,5,6,7,8 from information_schema.tables-- -
After this the hacker then finally uses the table which is usable for him and tries to find out the admin password for logging in the database.
http://www.demo[.]com/faculty/profile.php?id=96' union select group_concat(id,0x3a,uname,0x3a,upassword),2,3,4,5,6,7,8 from useraccounts-- -
So this are a demo of some main steps that a hacker follow during the SQL Injection.