
Open-Source Internship opportunity by OpenGenus for programmers. Apply now.

“Hackers find more success with organizations where employees are under appreciated, over worked and under paid. Why would anyone in an organization like that care enough to think twice before clicking on a phishing email?”
― James Scott, Sr. Fellow, Institute for Critical Infrastructure Technology
Phishing
From Wikipedia, the free encyclopedia
Not to be confused with Fishing or Pishing.
Phishing is a type of social engineering where an attacker sends a fraudulent ("spoofed") message designed to trick a human victim into revealing sensitive information to the attacker or to deploy malicious software on the victim's infrastructure like ransomware. Phishing attacks have become increasingly sophisticated and often transparently mirror the site being targeted, allowing the attacker to observe everything while the victim is navigating the site, and transverse any additional security boundaries with the victim. As of 2020, phishing is by far the most common attack performed by cyber-criminals, with the FBI's Internet Crime Complaint Centre recording over twice as many incidents of phishing than any other type of computer crime.
The first recorded use of the term "phishing" was in the cracking toolkit AOHell created by Koceilah Rekouche in 1995, however it is possible that the term was used before this in a print edition of the hacker magazine 2600. The word is a leetspeak variant of fishing (ph is a common replacement for f), probably influenced by phreaking, and alludes to the use of increasingly sophisticated lures to "fish" for users' sensitive information.
Attempts to prevent or mitigate the impact of phishing incidents include legislation, user training, public awareness, and technical security measures
What are phishing Campaigns
So my friends here i am back with a new article about phishing Campaigns, so let us begin, i bet you ask yourself what are actually this damn phishing Campaigns?
Your employees one day will receive some suspect phishing mails, maybe not so suspect because malicious attackers have everyday new tricks and ideas how they can fool you and your workers.
I guess all emails clients and your emploeeys are getting better and better at filtering them out, but they’re not perfect.
You want to hear some numbers and statistics?
Phishing remains one of the top access points for data breaches (2020 Verizon Data Breach Investigations Report)
94% of malware is delivered by email (CSO Online)
More than a quarter of U.S. employees admitted struggling to identify a phishing email (2020 State of Privacy and Security Awareness Report)
So you still asking you if phishing is dangerous and if its important to protect you and your employees against this?
Types of Phishing
There are many types of phishing as you can think so i am going to introduce some of them to you:
- Email Phishing
- Spear Phishing
- Clone Phishing
- Page Phishing
- Web page Phishing
Email phishing
There is something like bulk phishing, sending many phishing email to a non targeted person or company. Credentials or info that got compromised will be often used as a jumping point to another attacks to steal money or installing malware on the victims host. Streaming accounts credentials that got compromised will be often sold directly to a private person or sold in hacker forums or darknet.
Spear phishing
Spear phishing is a the "opposite" of the non targeted email, bulk phishing. In contrast to bulk phishing, spear phishing is something about to get targeted information and use it against for example executives or people that work in financial departments. So the attacker can get access to the company's sensetive data and services.
A 2019 study showed that accountancy and audit firms are frequent targets for spear phishing owing to their employees' access to information that could be valuable to criminals.
Threat Group-4127 (Fancy Bear) used spear phishing tactics to target email accounts linked to Hillary Clinton's 2016 presidential campaign. They attacked more than 1,800 Google accounts and implemented the accounts-google.com domain to threaten targeted users.
Clone phishing
Clone phishing is a type of phishing attack where attackers sendnig a nicely crafted email that are similar to a legitimate email that you actually can get from services that you use daily. The attachment or link within the email is replaced with a malicious version and that is perilous because it can be really irritating.
It may claim to be a resend of the original or an updated version to the original. Typically this requires either the sender or recipient to have been previously hacked for the malicious third party to obtain the legitimate email.
Page hijacking
Page hijacking is also dangerous technique that can be performed by performedan experienced attacker in order to redirect victims to a malicious webpage or an exploit kit through the xss cross site scripting. A hacker may compromise a legit webpage and insert an exploit kit such as MPack. Also often attackers just phish login credentials while using already compromised website.
Web page phishing
Simple form of phishing where malicios attacker creating a phishing page for example of a known service like Facebook, instagram or PayPal via copying the source code of a legit page and rewrite the code a little bit so if somebody logs there in all the comproside credentials will be saved in the malicious attacker database.
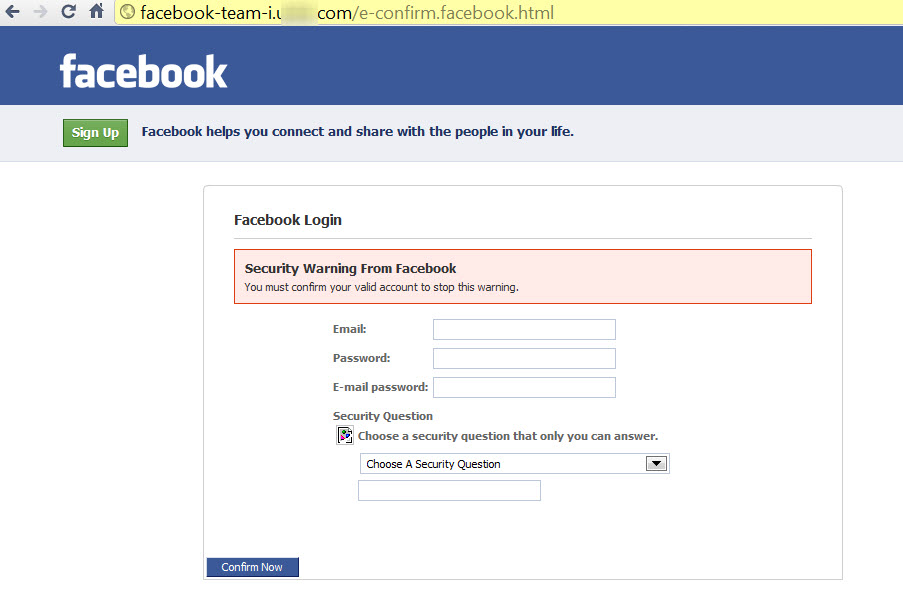
How To Recognize Phishing and prevent Phishing?
-
You have to know how phishing looks like
Learn baout new attack vectors, there are many webpages about the newest cyber security threats and also phishing attacks, be informed - be prepared! -
Don’t click all the links in your email folder and internet
Its generally a bad idea to click evrything you see, be really carefully what you click on. -
Don't give your sensetive data or information to the untrusted pages
If the URL of the website doesn’t start with “https”, or you cannot see a closed padlock icon next to the URL, do not enter any sensitive information or download files from that site. Site’s without security certificates may not be intended for phishing scams, but it’s better to be safe than sorry.
-
Rotate passwords regularly
Many of people use always the same password and usernames for all pages and never change them. Don't do this!
Try to update you passwords and don't use simillar passwords all the time, you can also think about password manager. -
Don't let the pop ups tempt you
Pop ups can be very confusing and irritating be careful they can contain malware that will be automatically downloaded to your pc if you click on them. Many attackers use panic techniques to make victims afraid telling them there are too many viruses on the pc and letting them install malicious programms. -
Have a Data Security Platform to spot signs of an attack
If you are unfortunate enough to be the victim of a successful phishing attack, then it’s important you are able to detect and react in a timely manner. Having a data security platform in place helps take some of the pressure off the IT/Security team by automatically alerting on anomalous user behavior and unwanted changes to files. If an attacker has access to your sensitive information, data security platforms can help to identify the affected account so that you can take actions to prevent further damage.
Be careful in the wild and don't let them phish you!
pic from: nordvpn.com/de/blog/what-is-phishing

